Data Masking 101: What Is It and How Does It Work? A Simple Explanation for Beginners

Data breaches cost companies millions. The 2021 Cost of Data Breach Report found the average cost of a data breach is $4.24 million. With stakes this high, safeguarding sensitive data is a top priority. This is where data masking comes in.
Data masking hides sensitive information to protect it from unauthorized access. It substitutes real data with realistic but fake data. This preserves the format and patterns in a dataset.
Data masking hides real data in systems. It replaces sensitive details with fictional data.
Masking matters a lot today. It protects privacy in many processes. This article explains data masking simply for beginners.
It covers:
- What data masking is
- Why it is important
- How data masking works
- Real-world examples
- Best practices for data masking
- Common questions on the topic
Why Is Data Masking Important?
Data breaches often lead to identity theft, financial fraud, and compliance violations. They damage consumer trust and a company’s reputation.Understanding data masking meaning is crucial in the context. Data masking limits the impact of data breaches by masking sensitive information. It also allows companies to share sample data for testing and development.
Data privacy laws like GDPR and HIPAA also mandate data protection. Data masking helps companies comply by de-identifying personal data.
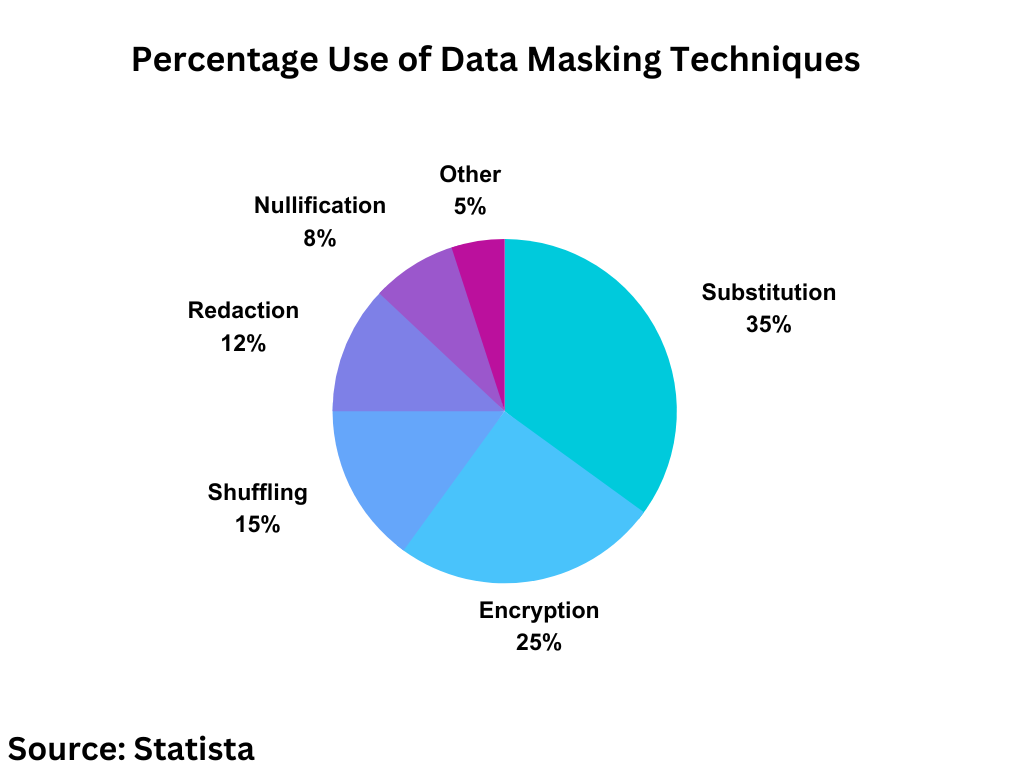
Data Masking Techniques
There are several techniques to mask sensitive data:
Substitution
This replaces real data with fake but realistic data. For example, substituting 123 Main Street with 765 Oak Avenue. Key benefits:
- Preserves data format, structure and patterns
- Maintains referential integrity in datasets
Shuffling
This mixes up data by swapping values between records. For example, shuffling phone numbers between customer records. Benefits:
- Retains a pool of real data
- Maintains data type and validity
Encryption
This encodes data using mathematical algorithms. Only authorized parties can decrypt it. Benefits:
- Strong protection for sensitive data
- Reversible process to access original data when needed
Redaction
This removes portions of data. For example, redacting credit card numbers except the last four digits. Benefits:
- De-identified data
- Meets strict compliance requirements
Nullification
This replaces data with nulls or blanks. Benefits:
- Removes data.
- Allows basic data analytics like counting records
Data Masking In Action
Data masking has become an essential data protection technique . Across many industries dealing with sensitive personal and financial information. Let’s explore some real-world applications. Also few examples of how data masking got deployed to safeguard critical data assets.
Healthcare
Healthcare organizations have some of the most sensitive personal data. Ranging from names and birthdates to medical histories, treatment plans and insurance details. Patient privacy is paramount. HIPAA mandates that healthcare providers install safeguards like data masking. To de-identify protected health information (PHI) for any secondary uses.
For instance, organizations must mask patient data before using it. It helps for testing new medical systems, training AI models. Also helps in conducting research studies or performing analytics.
Data masking techniques like substitution and shuffling transform identifying fields in patient records. They were realistic but fake data. This allows developing, testing and optimizing healthcare software without exposing real patient data. Data masking is also used to share sample patient data with medical researchers. Also to third party partners in a HIPAA compliant manner.
Finance
Banks and financial institutions manage confidential customer data. Data breaches in finance can destroy customer trust and trigger massive fraud. Hence, rigorous data protection becomes an important aspect.
Data masking allows financial organizations to share sample customer data. That helps them for testing new mobile apps and banking systems. Masking sensitive fields in transaction records lets developers build and refine software.
Banks also leverage data masking to create synthetic customer data. That helps to overcome training AI fraud detection models. Data masking transforms sensitive information. While maintaining the patterns required for accurate AI training. Financial firms are also using data masking for better privacy compliance. When outsourcing operations and analytics to third-party fintech vendors.
E-commerce
Online retailers need to protect customer personal and payment data. Data masking helps create safe customer data samples. That helps for testing new apps and websites.
Human resources
HR teams mask employee data like salaries and performance reviews before analysis. This allows insights without exposing sensitive information.
Challenges and Best Practices
Data masking brings its share of challenges:
Maintaining data quality
Masking can reduce data quality, impacting analytics and operations. Start with non-sensitive data and keep masked samples small.
Reversibility
Some use cases must access original data. Use reversible masking methods like encryption for such needs.
Masking all instances
Data duplicated across systems must got masked. Mask at early stages before propagation.
Securing data pipelines
Masking must ensure secure data pipelines. Prevent unmasked data leakage during ETL processes.
Monitoring data access
Continue monitoring masked datasets to detect unauthorized access attempts.
Testing
Test masked data in sandbox environments before deploying to production systems.
Best practices include:
- Mask based on use case, data sensitivity and access levels
- Use layered masking for high-risk data
- Mask data as close to source as possible
- Limit masked data sample sizes
- Mask data even across trusted internal teams
- Watch masked data access and pipelines
Key Takeaways
Data masking substitutes real data with fake data to limit data breach impact. It helps protect sensitive information and install privacy regulations. Organizations should check their needs. install layered masking plus complementary security controls for robust data protection.
This intro guides beginners through the basics of data masking. Companies dealing with critical data should explore data masking solutions with expert guidance. Then you can create secure and useful masked datasets.
Conclusion
Data masking is fast becoming vital for data security as breaches grow in scale and cost. A nuanced understanding of data masking techniques helps organizations mask. Following best practices further ensures robust protection. Embracing principled and thoughtful data masking is key to future-proofing data security.
FAQs
- How does data masking differ from encryption?
Encryption encodes original data which can got decrypted later if needed. Masking substitutes fake data . Encryption for reversible protection.
- Can data masking prevent data breaches completely?
Data masking reduces breach impact by hiding original data. But, it is one part of a defense-in-depth security strategy. Strong access controls, firewalls, employee training etc. are still needed.
- What are the limitations of data masking?
Data masking can impact data utility. Thus it may affect analytics, machine learning and operations. It also requires complex implementation and management.



