Streamlined Access: The Progress of Automated User Provisioning in the Current Journey
When user provisioning was handled manually, it took new hires a while to access the needed apps. The same applies to employees who had to switch roles. Simultaneously, former employees have a small window of time to access company data and compromise its integrity.
In the digital age, enterprise security relies on identity and access management (IAM). To prevent unsavory outcomes, provisions and de-provisions have to be handled. It should be accomplished quickly and intelligently. Automating user provisioning proves pivotal in streamlining identity lifecycles.. At the same time, it enhances governance and compliance.
This article will explore the changes and future trajectory of automated provisioning. It will highlight the benefits, mechanics, features, and challenges of automated provisioning.
The Changes in Identity Management in the Digital Era
Identity management has evolved from a manual process to an automated system.
Tracing the Shift to Automated User Provisioning
Traditionally, user provisioning was a manual process. It is the creation, access assignment, and removal of identities. This was workable when organizations were smaller. However, the enterprises digitized processes and grew exponentially. Manual approaches became highly inefficient and error-prone, posing serious security risks. Automating user provisioning through IAM solutions became imperative. It is necessary for managing identities and securing access at scale.
Integration of IAM Systems in Modern Enterprises
Digital identities and access requirements are ballooning. Modern enterprises now integrate sophisticated Identity and Access Management (IAM) systems. They enable automated user provisioning. Streamlined identity lifecycle management is essential. It is a given in today’s vast IT landscapes and remote work models. The $26.29 billion IAM market reflects the large-scale adoption of automated identity management.
Automated Provisioning for Streamlined IT Management
Automating identity lifecycles enables rapid, accurate provisioning. It can be aligned with roles and responsibilities. This is indispensable for streamlining security and access compliance across complex IT environments. Automated provisioning is a linchpin in connecting security policies to actual access enforcement.
The Inner Workings of Automated User Provisioning
Automated user provisioning employs an IAM platform with predefined settings. It works by customizing permissions and resource access. The company creates rules that automatically give new users access rights. It will depend on their role, group, and company policies. With predefined conditions, users have access and proper permissions for needed applications.
If a company onboards new sales reps, they know what software is needed by that group. Thus, they’ll have access to CRM software and the IT team can create a workflow. Once it’s activated in the IAM tool, all new reps will have a CRM account with standard features and privileges. They will also be given the needed credentials for system access.
A similar workflow would simultaneously apply to other network resources needed for that role. Examples of these include a cloud drive with sales materials and commission tracking systems. If the sales rep were to resign, the IT team could update their status in the IAM system. It will be automatic and immediate revocation of access rights to all apps. If the rep got promoted, the workflow would expand their privileges automatically.
The Mechanics of Automated User Provisioning
Understanding the mechanics of automated provisioning is crucial for seamless implementation.
The Identity Lifecycle
Automated provisioning manages the end-to-end identity lifecycle. It ranges from the creation of digital identities to the assignment of appropriate access rights. This process includes the deactivation of accounts—as per defined policies. Automation ensures access adjustments occur instantly when roles change or users leave organizations. This real-time provisioning enhances security tremendously.
Interplay with Service Delivery and Federation
Automated provisioning interlinks with service delivery systems and identity federation. They facilitate seamless access to resources across domains and platforms through single sign-on.. This interoperability facilitates a unified access experience.
Impact on Efficiency and Compliance
Automating provisioning processes dramatically improves provisioning velocity. It reduces compliance gaps due to lapses in access rights and strengthens monitoring This governance impact is evident in the $6.7 billion IGA market.
Advanced Features and Capabilities of Automated User Provisioning
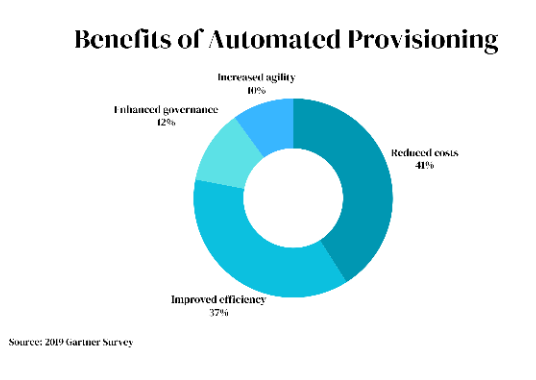
Sophisticated systems incorporate advanced capabilities beyond basic provisioning.
Authentication, Authorization, and Role Management
Secure multi-factor authentication, context-based dynamic authorization, and centralized role management. This enhances access control enforcement. By restricting access based on their role, automated user provisioning enhances security.
Delegation, Interchange, and Privacy
It has flexible identity delegation options, interchange standards, and built-in privacy controls. They enhance automation capabilities while preventing misuse.
From Basic Functions to Complex Ecosystems
Modern IAM solutions have changed from siloed provisioning to integrated, intelligent ecosystems. They are like the $2.65 billion PAM market segment. This eases access to governance at scale. As such, even small businesses can use automated provisioning and expect it to grow with them.
The Future of Automated User Provisioning: Trends and Innovations
Automated provisioning is poised for ongoing evolution.
The Emergence of Decentralized Identity Management
Blockchain and self-sovereign identity models are set to decentralize provisioning. This shift gives control to users while enhancing privacy.
The Role of Emerging Technologies and Standards
Technologies like AI-driven analytics and standards like SCIM will shape provisioning. They enable intelligent automation and enhance interoperability.
Integration of AI and Machine Learning
AI and ML will transform provisioning by enabling predictive, no-touch provisioning. At the same time, they are aligned to access patterns. This represents the next frontier.
Frequently Asked Questions
How does automation enhance security and ensure compliance?
Instantly propagate access changes. Automation minimizes lapses that lead to vulnerabilities and non-compliance while providing audit trails.
What are the key issues in implementing such systems?
Disparate legacy systems, inflexible designs impeding scalability, and lack of in-house integration expertise. They are common hurdles to seamless deployment.
How will AI and ML reshape the landscape of automated provisioning?
They will enable secure self-service provisioning, access forecasting, and anomaly detection. In effect, They make systems highly adaptable and resilient to emerging threats.
Conclusion
Automated user provisioning has progressed tremendously. It now delivers robust, streamlined access control. It is driven by innovation and underpinned by identity intelligence. With an eye on the future, companies can embark into increasingly digital frontiers.



