The Building Blocks of ZTNA – Understanding the Key Components
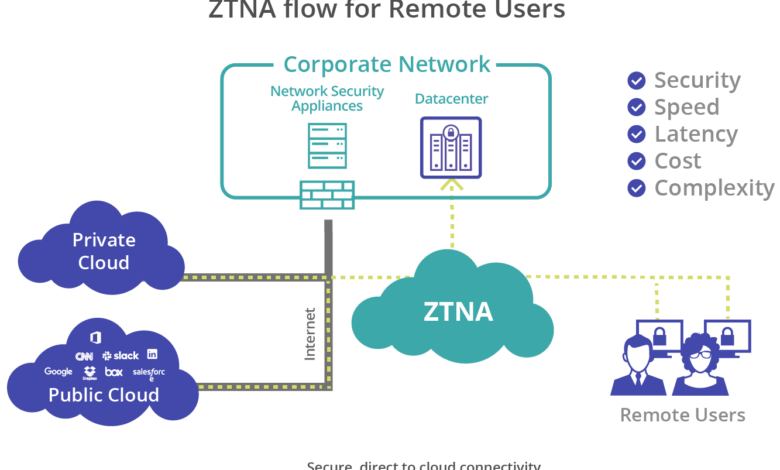
Many organizations will choose a service-based solution. This allows them to deploy and manage a zero-trust network access architecture without requiring an endpoint application or hardware installed on every device. Ensure the solution offers holistic control and visibility by integrating security, WAN optimization and network services. This provides the scalability and performance that remote workers need to be productive.
Identity Management
Identity management, sometimes called identity and access management (IAM), is an overarching discipline that combines policies and technologies to ensure the right users get the right level of access to technology resources. This includes registering, verifying and controlling users on computers. Identity management also manages descriptive information about each user, how that information can be accessed and modified by the system, and how access rights are revoked or re-established when a user changes roles or is offboarded from an organization.
To achieve these capabilities, a scalable directory service for storing the identities of all managed entities is required. This can be a central repository like Microsoft Active Directory, Apache Directory Studio or Lightweight Directory Access Protocol (LDAP). In addition to the directory services, a provisioning framework for linking the IAM with legacy or application-specific directories is also needed.
An essential component of IAM is authentication, which validates a digital user ID using credentials stored in a repository. IAM systems are typically designed to provide multifactor authentication (MFA), including the ability to use biometrics such as retinal scan, facial recognition, fingerprints and voice recognition for authenticating a user. IAM also includes facilities for registering, changing and resetting passwords. IAM also supports automating frequently performed IT and HR admin tasks to reduce the time, effort and human error associated with achieving them manually.
Privilege Management
Zero trust access is a security strategy that applies the Principle of Least Privilege to user and device authorization. It improves cybersecurity by continuously checking the identity of devices, users, and applications at every access level before allowing them to gain access to sensitive network resources. This ensures that unauthorized data does not leave the network and is not seen by hackers. It is also essential to understand how does ZTNA work. This framework’s implementation combines cutting-edge technologies like risk-based multi-factor authentication, identity protection, next-generation endpoint security, and reliable cloud workload technology to verify a user’s or system’s identity, take current access into account, and maintain system security. To implement zero trust, it is also necessary to consider email security, asset and endpoint hygiene, and data encryption.
Many organizations implement ZTNA when upgrading their IT infrastructure with SaaS applications and cloud services. This allows them to create software-defined perimeters, dividing their internal networks into multiple micro-segments and preventing attackers who breach a corporate firewall from moving freely throughout their IT environment.
In some cases, ZTNA can be a challenge for employees who may need to provide extra credentials or go through other processes before they are allowed to access their applications. Additionally, the network tunnels and encryption used in ZTNA can slow down network performance and impact employee productivity.
There are two main types of ZTNA: agent-based and service-initiated. In this model, an agent is installed on each end-user device that sends data about the device to a controller. The controller authenticates the machine and carries out a validation process. Once this has been done, all connections to the application are routed through a gateway and the outbound connection from the app is secured. This approach can be more effective at providing secure access for remote workers with BYOD and unmanaged devices.
Access Control
While organizations must securely connect remote employees, mobile workers, and customers to applications over the public internet, they also must minimize the risk of hackers accessing sensitive data. This is where zero trust access comes into play. Only authorized users can access applications by hiding apps and infrastructure from discovery over the public internet.
ZTNA solutions provide granular, context-aware access that improves security and the user experience. For example, when a contractor or vendor needs access to an internal application but can’t handle WAN latency, a ZTNA solution can bypass the centralized firewall and access the app directly. This reduces third-party risk and allows companies to avoid costly hardware upgrades.
To enable granular user-to-app access, the security software used by ZTNA must be able to determine whether the device and application meet policy requirements. This step usually includes verifying the identity of the device and user, checking for the presence of anti-virus software, validating device certificates, and ensuring that the application is configured appropriately.
Many available products for implementing a ZTNA strategy have these capabilities built in. However, some require additional tools to perform the functions. Some key considerations for choosing a solution include its level of integration with adjacent technologies, whether it supports legacy applications, and what type of connectivity it provides.
Security Analytics
A zero-trust architecture implements security analytics that evaluates the risk of users, devices and applications to identify and respond to threats. Security analytics can be context-aware, assessing factors like time of day or geographic location to determine whether an endpoint is trusted to access specific data. Security analytics can also detect patterns of behavior that indicate potential compromise, such as identifying the use of compromised user accounts and other indicators of lateral movement. Finally, security analytics can be used to prevent unauthorized access by securing network connectivity through a gateway that shields application servers from direct Internet connections and from users and devices that are not authorized to access them. This is known as micro-segmentation and limits the impact of a breach by preventing attackers from moving laterally across an organization’s infrastructure. ZTNA can be deployed as part of an integrated security stack that includes a cloud access security broker (CASB), secure web gateway and firewall-as-a-service. These solutions implement a security service edge (SASE) architecture to securely support the adoption of cloud, remote work and digital transformation initiatives.
Security suppliers often offer SASE architectures, including a gateway solution and the cloud access security broker or SWG components. This approach reduces the number of integration points and enables organizations to implement a zero-trust deployment quickly and easily.